SCIM Configuration Guide Instructions
This guide provides the steps required to configure Provisioning for Getabstract SCIM service, and includes the following sections
Instructions
- Features
- Requirements
- Configuration Steps
- Troubleshooting
Features
The following provisioning features are supported
Push New Users
New users created through OKTA will also be created in Getabstract.
Push Profile Updates
Updates made to the user's profile through OKTA will be pushed to Getabstract.
Push User Deactivation
Deactivating the user or disabling the user's access to the application through OKTA will deactivate the user in Getabstract.
Note: For this application, deactivating a user means updating the status from active to inactive, leaving the data intact but the user unable to sign in.
Push Groups
Groups and their members can be pushed to Getabstract.
Note: for this application, Groups means the users will have a column label assigned to the account profile, like Department, Location, etc.
Reactivate Users
User accounts can be reactivated through OKTA.
Note: If the user account was deactivated, it will be reactivated with access to their existing Getabstract account profile. If the user was hard deleted, a new account will be created.
Requirements
Before you configure provisioning for Getabstract, make sure you have SCIM 2.0 base Url and Oauth Api Credentials values, otherwise request to B2B.ITSupport@getabstract.com or with your Getabstract representative.
Before you can start using provisioning for Getabstract, configure the SSO SAML 2.0 for the Getabstract app.
Setup SSO for Getabstract in Okta
SSP SAML setup: https://saml-doc.okta.com/SAML_Docs/How-to-Configure-SAML-2.0-for-Getabstract.html
Configuration Steps
Configure your Provisioning settings for Getabstract.
- Add SCIM for Getabstract.
- Go to Provisioning tab and click on Configure API Integration.
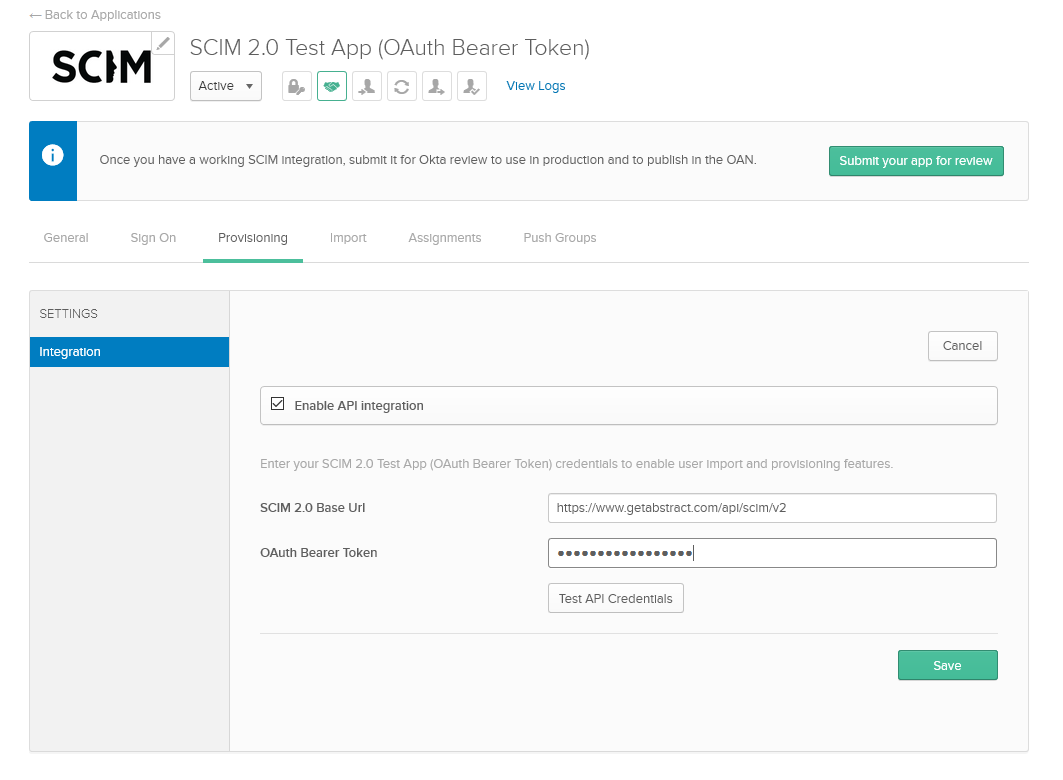
Check off Enable API Integration and enter the following values
SCIM 2.0 base Url
- TEST: https://int.getabstract.com/api/scim/v2
- PROD: https://www.getabstract.com/api/scim/v2
- TEST: key provided by Getabstract
- PROD: key provided by Getabstract
click on Save.
Troubleshooting and Tips
N/A
Disclaimer
N/A
